Cyber Security Consultant Essex: Secure Your Service from Hazards
Cyber Security Consultant Essex: Secure Your Service from Hazards
Blog Article
Releasing the One-upmanship: Exactly How IT Support Services and Cyber Security Drive Business Success
In the busy landscape of contemporary business, keeping a competitive side is vital for long-term success. As we discover the elaborate interaction between IT support solutions and cybersecurity in driving company success, a closer look discloses a transformative capacity that extends much beyond mere functional functionality.
Relevance of IT Assistance Services
Reliable IT support services are the foundation of functional continuity and performance in modern services. In today's electronic age, where innovation underpins virtually every aspect of operations, having trusted IT support is vital for smooth functioning. IT support solutions encompass a variety of features, including fixing technological concerns, maintaining hardware and software program systems, giving network safety, and supplying prompt assistance to individuals encountering IT-related obstacles.
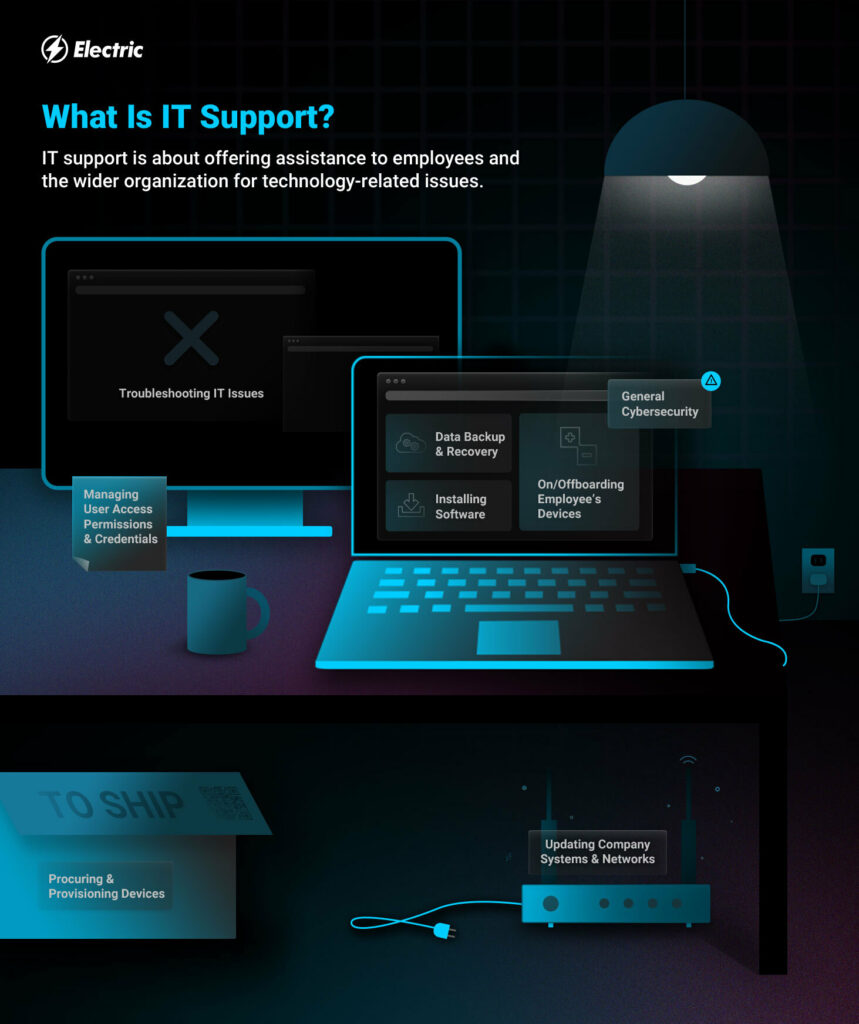
Additionally, IT sustain solutions play a vital duty in protecting data and systems from cyber risks. With the enhancing danger of cyberattacks, having durable IT sustain in position is important for securing delicate information and keeping the integrity of service procedures. By proactively implementing and monitoring systems safety procedures, IT sustain services help reduce dangers and make certain business connection.
Enhancing Functional Performance
To enhance service efficiency and streamline processes, operational effectiveness is paramount in today's competitive market. Enhancing functional effectiveness includes optimizing output with the least amount of input and resources. Applying IT support services and durable cybersecurity measures can significantly contribute to boosting functional effectiveness.
IT support services play a vital duty in maintaining smooth operations by giving prompt technological help, solving problems immediately, and ensuring that systems are up and running effectively. This aggressive technique reduces downtime, enhances efficiency, and permits workers to concentrate on core service tasks.
Additionally, cybersecurity measures are necessary for protecting delicate information, avoiding cyber hazards, and guaranteeing organization connection. By protecting useful details and systems from potential cyber-attacks, companies can stay clear of costly breaches that can interfere with procedures and damage track record.
Shielding Data and Properties
Securing sensitive information and properties is a crucial element of keeping a resilient and protected organization setting. In today's digital landscape, where cyber risks are ever-evolving, business need to focus on guarding their valuable information. Executing robust cybersecurity procedures, such as file encryption, multi-factor verification, and regular protection audits, is essential to safeguard data from unauthorized access and potential breaches. Moreover, creating backups of critical data and establishing safe gain access to controls assist reduce the risks associated with data loss or burglary.
Along with cybersecurity steps, physical security additionally plays a crucial function in safeguarding properties. Utilizing measures like security systems, gain access to control systems, and protected storage space centers can help prevent unapproved accessibility to physical assets (it support in essex). Furthermore, applying plans and procedures for possession management, consisting of inventory monitoring and regular audits, boosts overall protection procedures
Mitigating Cyber Threats
In the world of cybersecurity, proactive procedures are key to properly mitigating cyber risks. As modern technology advancements, so do the intricacies of cyber threats, making it essential for services to stay ahead of possible risks. Carrying out durable safety and security methods, such as regular safety and security audits, infiltration screening, and employee training, is necessary in safeguarding against cyber assaults.
Among the most common cyber risks dealt with by organizations is phishing strikes. These deceptive emails or messages aim to deceive people right into divulging sensitive information or clicking on malicious links. By informing staff members on just how to respond and identify to phishing attempts, organizations can substantially minimize their susceptability to such risks.
Furthermore, ransomware assaults remain to posture a considerable danger to businesses of all sizes. Consistently supporting data, maintaining updated protection software, and limiting user gain access to can assist minimize the influence of ransomware strikes.
Driving Organization Success
Maximizing functional performance and promoting advancement are important elements in driving business success in today's affordable landscape. Services that improve their operations via effective IT support solutions can designate resources more properly, causing cost savings and boosted efficiency. By leveraging cyber security actions, companies can safeguard their beneficial data and protect their online reputation, getting a competitive side on the market.
Furthermore, IT sustain services play a crucial role in boosting customer experience (cyber security consultant Essex). Quick resolution of technical problems and proactive maintenance make certain smooth operations, cultivating customer depend on and loyalty. This, consequently, converts into read repeat service and positive recommendations, driving earnings growth
Cutting-edge technologies supported by durable IT solutions enable services to adjust to changing market demands promptly. Whether through cloud other computing, information analytics, or automation, firms can stay ahead of the competitors and exploit on new chances. Welcoming digital improvement not just boosts effectiveness however additionally opens up doors to new income streams, solidifying the structure for lasting success.
Conclusion
Finally, the combination of IT sustain solutions and cyber security steps is necessary for organizations to maintain operational efficiency, protect useful information and properties, and minimize potential cyber dangers. By leveraging these modern technologies properly, organizations can acquire an one-upmanship in the market and drive general company success. It is imperative for companies Find Out More to prioritize investments in IT sustain and cyber security to ensure long-term sustainability and growth.
As we explore the intricate interplay between IT sustain services and cybersecurity in driving service success, a better look exposes a transformative potential that expands much beyond plain functional capability.

Services that improve their operations via effective IT support solutions can designate resources more effectively, leading to set you back savings and improved performance.In final thought, the integration of IT sustain services and cyber security actions is necessary for companies to maintain functional effectiveness, safeguard beneficial information and assets, and minimize prospective cyber threats.
Report this page